Windows cryptomining attacks target graphic designer's high-powered GPUs
Cybercriminals are leveraging a legitimate Windows tool called 'Advanced Installer' to infect the computers of graphic designers with cryptocurrency miners.
The attackers promote installers for popular 3D modeling and graphic design software such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, likely through black hat search engine optimization techniques.
However, these installers include hidden malicious scripts that infect downloaders with remote access trojans (RATs) and cryptomining payloads.
The threat actors are focusing on these specific targets as graphics designers, animators, and video editors are more likely to use computers with powerful GPUs that support higher mining hash rates, making the cryptojacking operation more profitable.
The campaign was discovered by Cisco Talos, which today reports it has been underway since at least November 2021.
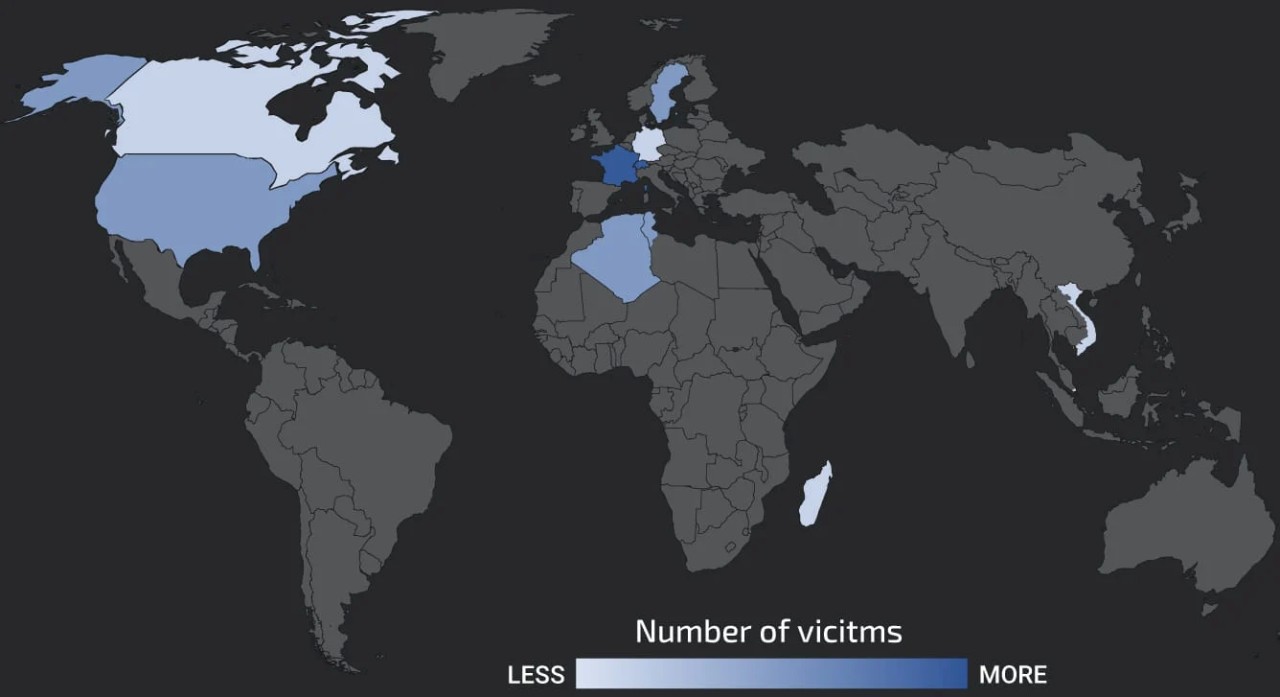
Currently, most of the victims are located in France and Switzerland, while there's also a notable number of infections in the United States, Canada, Germany, Algeria, and Singapore.
Two attack methods
Cisco's analysts have observed two distinct attacks used in this campaign.
In both cases, the attackers use Advanced Installer to create installer files for Windows packed with malicious PowerShell and batch scripts that are executed upon the installer's launch through the software's "Custom Action" feature.
The two attack methods differ in the scripts executed, the complexity of the infection chain, and the final payloads dropped on the target device.
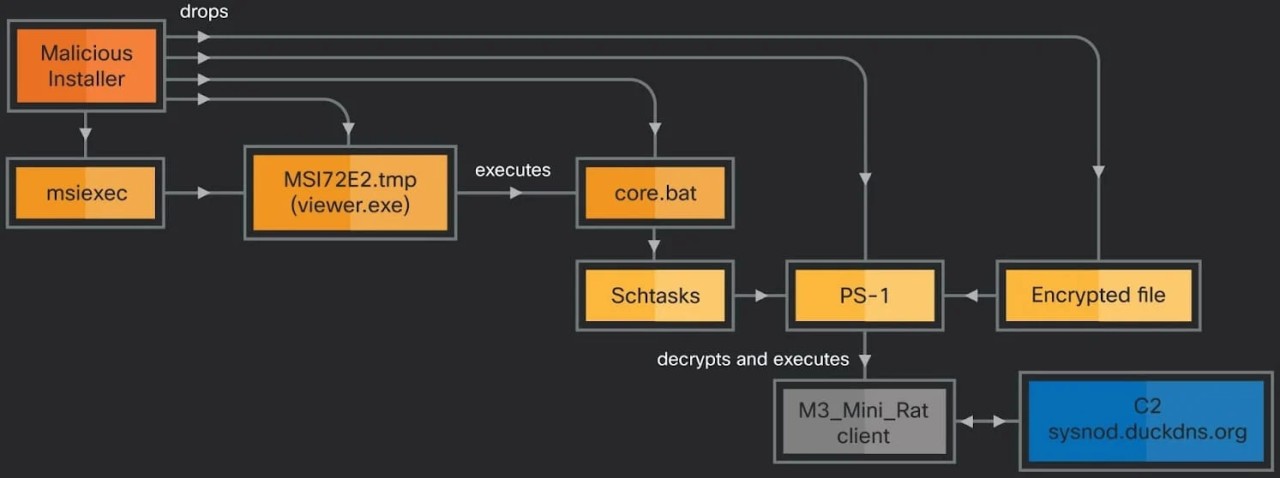
The first method uses a batch script (core.bat) to set up a recurring task running a PowerShell script that decrypts the final payload (M3_Mini_Rat).
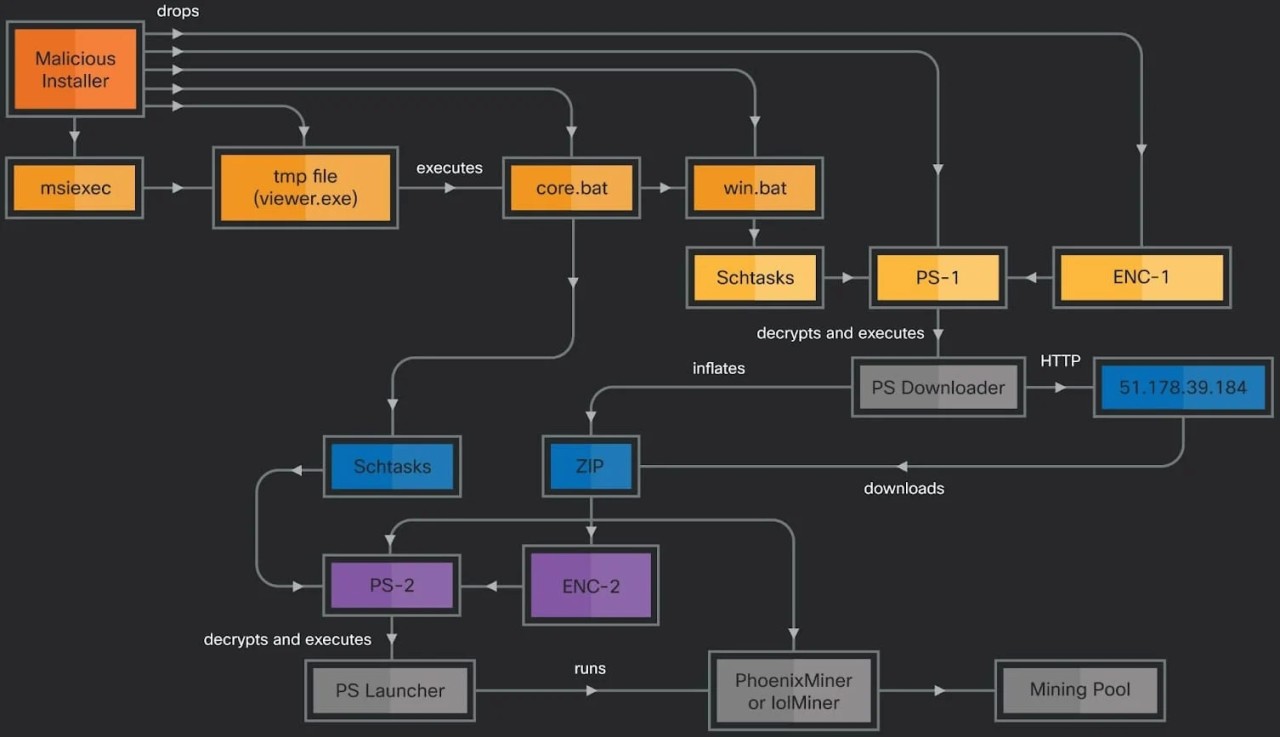
The second attack method drops two malicious scripts, core.bat and win.bat, that set up scheduled tasks to run PowerShell scripts.
The PowerShell executed by the win.bat file decrypts a downloader script and fetches a ZIP archive containing a payload (PhoenixMiner or lolMiner), a second PS script (which core.bat schedules for), and another encrypted file.
The first method, which delivers a backdoor payload, could be chosen by the attackers in cases where maintaining discreet, prolonged access to target systems is the primary goal.
The second attack method, which employs cryptominers, is geared towards swift financial gains at a higher risk of detection.
Mining and RAT payloads
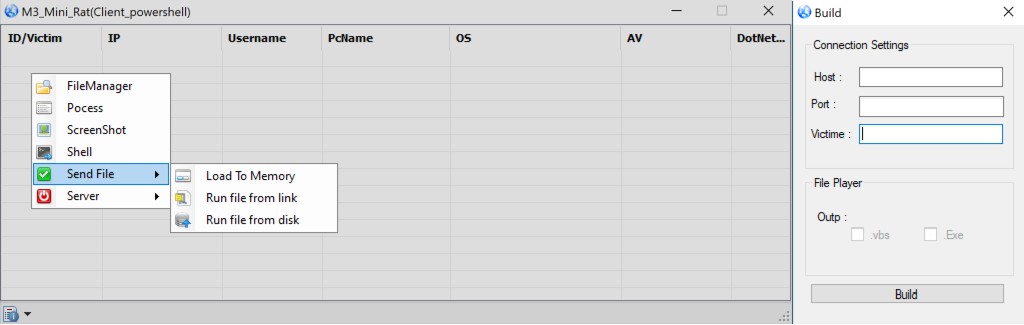
The M3_Mini_Rat payload gives the attackers remote access capabilities, enabling them to perform system reconnaissance and install additional payloads on the infected system.
The RAT tool can perform the following functions:
- System Reconnaissance: Gathers details like username, OS version, anti-virus status, network status, and hardware specs.
- Process Management: Lists and manages running processes, including termination capabilities.
- File System Exploration: Enumerates logical drives and retrieves details of specific folders.
- Command & Control: Uses a TCP connection for remote administration tasks and command receipt.
- File Management: Handles downloading, checking, renaming, and deleting files, and can execute malicious binaries.
- Data Transmission: Sends data, including reconnaissance details, back to the attacker's server.
- Special Checks: Identifies specific server processes, like the Citrix connection center server.
- Exit: Offers ways to securely exit the client and manage its data streams.
The other two payloads, PhoenixMiner and lolMiner, mine cryptocurrency by hijacking the computational power of AMD, Nvidia, and Intel (lolMiner only) graphics cards.
PhoenixMiner is an Ethash (ETH, ETC, Musicoin, EXP, UBQ, etc.) miner, while lolMiner supports multiple protocols including Etchash, Autolykos2, Beam, Grin, Ae, ALPH, Flux, Equihash, Kaspa, Nexa, Ironfish and others.
The lolMiner version spotted in this campaign is 1.76, which supports simultaneous mining of two different cryptocurrencies.
The PhoenixMiner configuration sets the GPU power limit to 75% and the system fun control max speed to 65%.
Similar restrictions are seen in the lolMiner parameters, which uses 75% of the GPU power and pauses mining if the temperature reaches 70 degrees Celsius.
This indicates that the attackers try to avoid being detected by using too many resources.
A full list of the indicators of compromise for this campaign can be found on this GitHub repository.


Comments