Russian hackers target govt orgs in Microsoft Teams phishing attacks
Microsoft says a hacking group tracked as APT29 and linked to Russia's Foreign Intelligence Service (SVR) targeted dozens of organizations worldwide, including government agencies, in Microsoft Teams phishing attacks.
"Our current investigation indicates this campaign has affected fewer than 40 unique global organizations," Microsoft revealed today.
"The organizations targeted in this activity likely indicate specific espionage objectives by Midnight Blizzard directed at government, non-government organizations (NGOs), IT services, technology, discrete manufacturing, and media sectors."
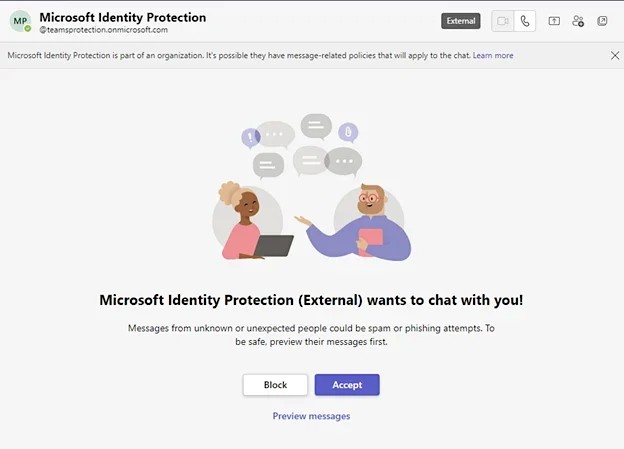
The threat actors utilized compromised Microsoft 365 tenants to create new technical support-themed domains and send tech support lures, attempting to trick users of the targeted organizations using social engineering tactics.
They aimed to manipulate users into granting approval for multifactor authentication (MFA) prompts, ultimately aiming to steal their credentials.
The attackers created new domains using compromised Microsoft 365 tenants with a technical support theme. These new domains were part of the 'onmicrosoft.com' domain, a legitimate Microsoft domain that is automatically used by Microsoft 365 for fallback purposes in case a custom domain is not created.
They then employed these domains to send tech support lures to deceive users from targeted organizations into approving multifactor authentication (MFA) prompts.
As the messages came from the legitimate onmicrosoft.com domain, they may have caused the fake Microsoft support messages to appear trustworthy.
According to Redmond's advisory, the ultimate objective of the threat actors was to steal the targeted users' credentials.
"In some cases, the actor attempts to add a device to the organization as a managed device via Microsoft Entra ID (formerly Azure Active Directory), likely an attempt to circumvent conditional access policies configured to restrict access to specific resources to managed devices only," Microsoft added.
The company reports having successfully blocked the Russian threat group from utilizing the domains in other attacks and is now actively working to address and mitigate the campaign's impact.
Not all bugs are created equal
Last month, Microsoft refused to address a security issue in Microsoft Teams (discovered by Jumpsec security researchers) that can let anyone bypass restrictions for incoming files from external tenants using a Python tool named TeamsPhisher, developed by Alex Reid, a U.S. Navy's Red team member.
When JumpSec reported the bug in June, Microsoft said the flaw "does not meet the bar for immediate servicing."
BleepingComputer also contacted Microsoft to ask if there are any plans to fix this issue and was told that customers should pay attention to suspicious messages.
"We're aware of this report and have determined that it relies on social engineering to be successful," a Microsoft spokesperson told BleepingComputer.
"We encourage customers to practice good computing habits online, including exercising caution when clicking on links to web pages, opening unknown files, or accepting file transfers."
Unfortunately, APT29's social engineering attack also impacted government agencies, highlighting the considerable impact such attacks can have, even on well-protected entities.
Russia's foreign intelligence hackers
APT29, the Russian Foreign Intelligence Service (SVR) hacking division, orchestrated the SolarWinds supply-chain attack that led to the breach of several U.S. federal agencies three years ago.
Since that incident, this hacking group has also infiltrated other organizations' networks using stealthy malware, including TrailBlazer and a variant of the GoldMax Linux backdoor, which allowed them to remain undetected for years.
More recently, Microsoft disclosed that the hacking group is using new malware capable of seizing control of Active Directory Federation Services (ADFS) to log in as any user in Windows systems.
Furthermore, they have targeted Microsoft 365 accounts belonging to entities in NATO countries as part of their efforts to gain access to foreign policy-related information.
Additionally, they were behind a series of phishing campaigns, explicitly targeting governments, embassies, and high-ranking officials throughout Europe.


Comments