New BLUFFS attack lets attackers hijack Bluetooth connections
Researchers at Eurecom have developed six new attacks collectively named 'BLUFFS' that can break the secrecy of Bluetooth sessions, allowing for device impersonation and man-in-the-middle (MitM) attacks.
Daniele Antonioli, who discovered the attacks, explains that BLUFFS exploits two previously unknown flaws in the Bluetooth standard related to how session keys are derived to decrypt data in exchange.
These flaws are not specific to hardware or software configurations but are architectural instead, meaning they affect Bluetooth at a fundamental level.
The issues are tracked under the identifier CVE-2023-24023 and impact Bluetooth Core Specification 4.2 through 5.4.
Considering the widespread use of the well-established wireless communication standard and the versions impacted by the exploits, BLUFFS could work against billions of devices, including laptops, smartphones, and other mobile devices.
How BLUFFS works
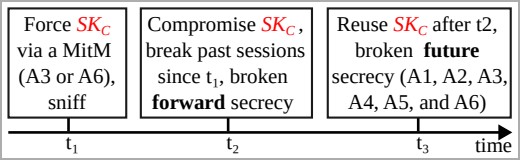
BLUFFS is a series of exploits targeting Bluetooth, aiming to break Bluetooth sessions' forward and future secrecy, compromising the confidentiality of past and future communications between devices.
This is achieved by exploiting four flaws in the session key derivation process, two of which are new, to force the derivation of a short, thus weak and predictable session key (SKC).
Next, the attacker brute-forces the key, enabling them to decrypt past communication and decrypt or manipulate future communications.
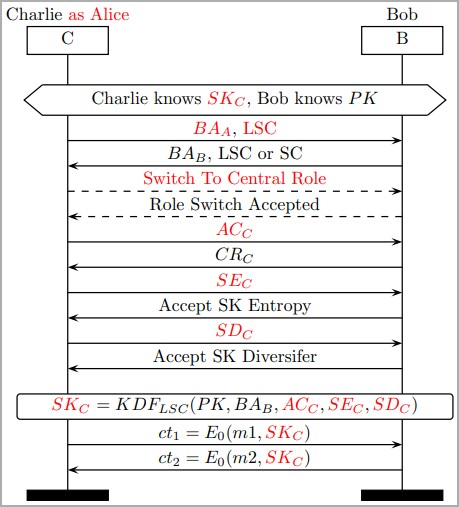
Executing the attack presupposes that the attacker is within Bluetooth range of the two targets that exchange data and impersonates one to negotiate for a weak session key with the other, proposing the lowest possible key entropy value and using a constant session key diversifier.
The published paper presents six types of BLUFFS attacks, covering various combinations of impersonating and MitM attacks, which work regardless of whether the victims support Secure Connections (SC) or Legacy Secure Connections (LSC).
The researchers developed and shared a toolkit on GitHub that demonstrates the effectiveness of BLUFFS. It includes a Python script to test the attacks, the ARM patches, the parser, and the PCAP samples captured during their tests.
Impact and remediation
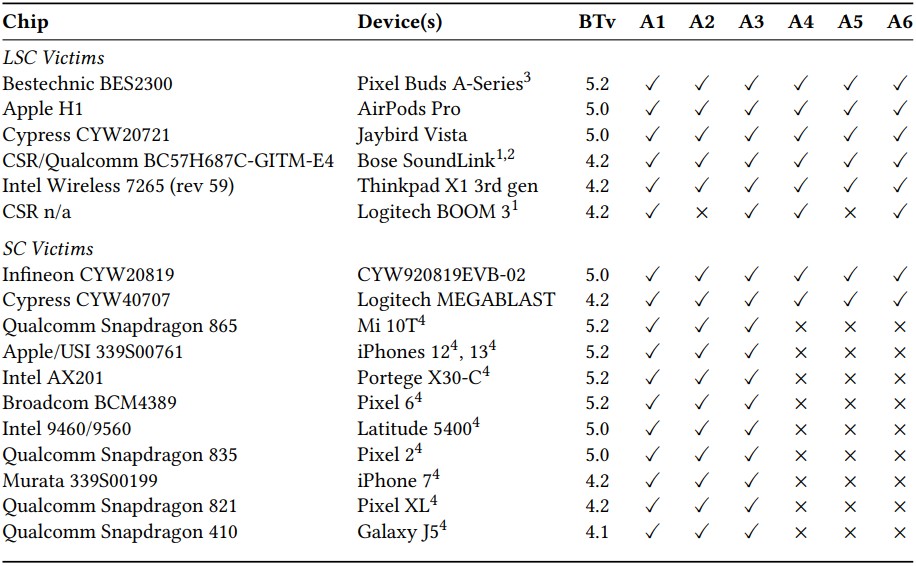
BLUFFS impacts Bluetooth 4.2, released in December 2014, and all versions up to the latest, Bluetooth 5.4, released in February 2023.
The Eurecom paper presents test results for BLUFFS against various devices, including smartphones, earphones, and laptops, running Bluetooth versions 4.1 through 5.2. All of them were confirmed to be susceptible to at least three out of six BLUFFS attacks.
The paper also proposes the following backward-compatible modifications that would enhance session key derivation and mitigate BLUFFS and similar threats:
- Introduce a new "Key Derivation Function" (KDF) for Legacy Secure Connections (LSC) that involves mutual nonce exchange and verification, adding minimal overhead.
- Devices should use a shared pairing key for the mutual authentication of key diversifiers, ensuring the legitimacy of session participants.
- Enforce Secure Connections (SC) mode where possible.
- Maintain a cache of session key diversifiers to prevent reuse.
Bluetooth SIG (Special Interest Group), the non-profit organization that oversees the development of the Bluetooth standard and is responsible for licensing the technology, has received Eurecom's report and published a statement on its site.
The organization suggests that implementations reject connections with low key strengths below seven octets, use 'Security Mode 4 Level 4', which ensures a higher encryption strength level, and operate in 'Secure Connections Only' mode when pairing.

Comments