LockBit ransomware exploits Citrix Bleed in attacks, 10K servers exposed
The Lockbit ransomware attacks use publicly available exploits for the Citrix Bleed vulnerability (CVE-2023-4966) to breach the systems of large organizations, steal data, and encrypt files.
Although Citrix made fixes available for CVE-2023-4966 more than a month ago, thousands of internet-exposed endpoints are still running vulnerable appliances, many in the U.S.
High-profile Lockbit attacks
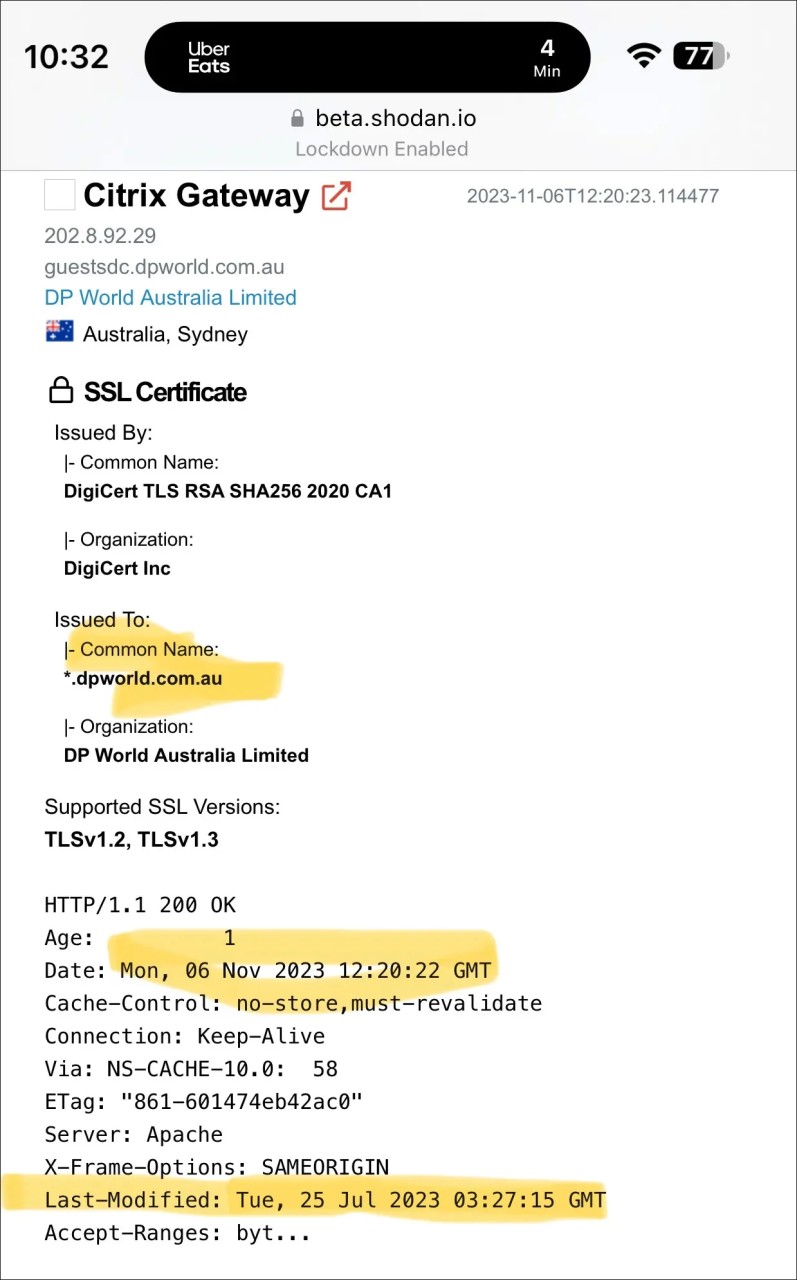
Threat researcher Kevin Beaumont has been tracking attacks against various companies, including the Industrial and Commercial Bank of China (ICBC), DP World, Allen & Overy, and Boeing, and found they had something in common.
These are exposed Citrix servers [1, 2] vulnerable to the Citrix Bleed flaw, which he says the LockBit ransomware gang is exploiting attacks.
This was further confirmed by the Wall Street Journal, which obtained an email from the U.S. Treasury sent to select financial service providers, mentioning that LockBit was responsible for the cyberattack on ICBC, which was achieved by exploiting the Citrix Bleed flaw.
If LockBit used the vulnerability to breach one company, it is believed they likely breached Boeing and DP World similarly.
These attacks are likely being conducted by a LockBit affiliate who is heavily utilizing this vulnerability to breach networks rather than the ransomware operation itself being behind the attack.
As LockBit is the largest Ransomware-as-a-Service, it utilizes many affiliates who have complete discretion on how they breach networks.
As we saw with an affiliate who belonged to both the GandCrab and then REvil operations, it is not uncommon for a hacker to focus on one particular industry or initial access method.
For example, a GandCrab/REvil affiliate specialized in exploiting MSP software [1, 2, 3] to encrypt companies, and we are likely seeing a LockBit affiliate utilizing the Citrix Bleed flaw to mass-breach networks.
A massive attack surface
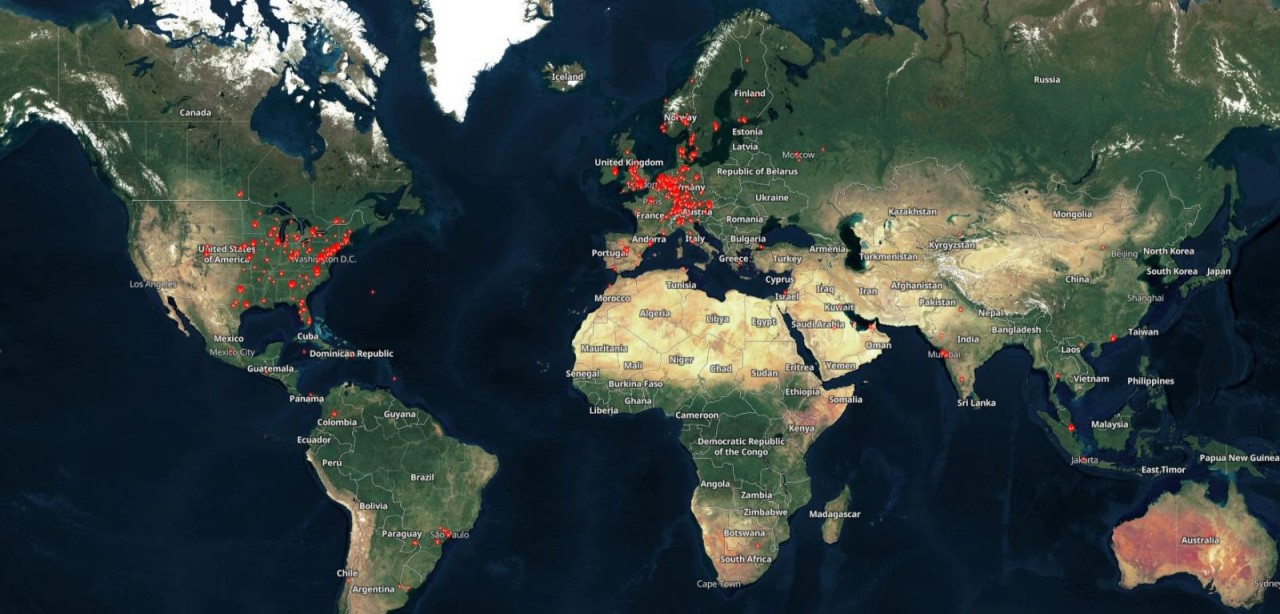
At the time of writing, more than 10,400 Citrix servers are vulnerable to CVE-2023-4966, according to findings from Japanese threat researcher Yutaka Sejiyama.
The majority of the servers, 3,133, are in the U.S., followed by 1,228 in Germany, 733 in China, 558 in the U.K., 381 in Australia, 309 in Canada, 301 in France, 277 in Italy, 252 in Spain, 244 in the Netherlands, and 215 in Switzerland.
Sejiyama's scans have revealed vulnerable servers in large and critical organizations in many other countries, all of which remain unpatched over a full month following the public disclosure of the critical flaw.
Citrix Bleed details
Citrix Bleed was disclosed on October 10 as a critical security issue that affects Citrix NetScaler ADC and Gateway, enabling access to sensitive device information.
Mandiant reported that threat actors started exploiting Citrix Bleed in late August, when the security flaw was still a zero day. In the attacks, hackers used HTTP GET requests to obtain Netscaler AAA session cookies after the multi-factor authentication stage (MFA).
Citrix urged admins to protect systems from this low-complexity, no-interaction attacks. On October 25, external attack surface management company AssetNote released a proof-of-concept exploit demonstrating how session tokens can be stolen.


Comments