How company size affects the email threats targeting your business
It takes less than a minute for someone to fall for a phishing scam. According to the 2024 Data Breach Investigations Report, the median time for a recipient to click on a malicious link after opening the email is 21 seconds, followed by 28 seconds to enter the requested data.
Email-based attacks are not just fast — they are widespread and successful. This is because they are relatively low cost and easy to implement and can be scaled and adapted as new tools and capabilities become available.
A new top email threats and trends report shows a steady year-on-year increase in targeted email threats such as business email compromise (BEC) and conversation hijacking. In this blog we explore how the type and prevalence of targeted email threats can vary according to company size.
Barracuda's email threat detection data from early June 2023 to the end of May 2024 shows that companies of different sizes have different risk profiles when it comes to the type of email attacks they receive.
We have focused our analysis on targeted email attacks, including phishing, business email compromise, and conversation hijacking.
The volume of targeted phishing attacks by company size
In terms of phishing, the largest organizations, with 2,000 or more mailboxes, received an average of around 7,500 phishing threats over the course of 12 months. However, individual mailboxes were hit on average only once in the same period.
This rises to six incidents per mailbox for the smallest firms, a significantly higher risk despite the average of only around 180 attacks overall.
This disparity could be related to the different organizational structures and resourcing in companies of different sizes. For example, smaller companies tend to have flatter organizational structures with easier access to names or contact details. This could mean that attackers can target a wide range of employees.
Due to their smaller size, they are also likely to have more people with privileged access to data and systems. There are fewer degrees of separation between employees, enabling attackers to move laterally quickly. As a result, inbound attack emails are more evenly distributed across the business and could target the intern as well as the CEO.
At a larger organization, high-value, privileged accounts are usually concentrated among a few individual employees or company leaders. These users may often receive the bulk of the attacks, while many other mailboxes receive no inbound threats at all, bringing down the average.
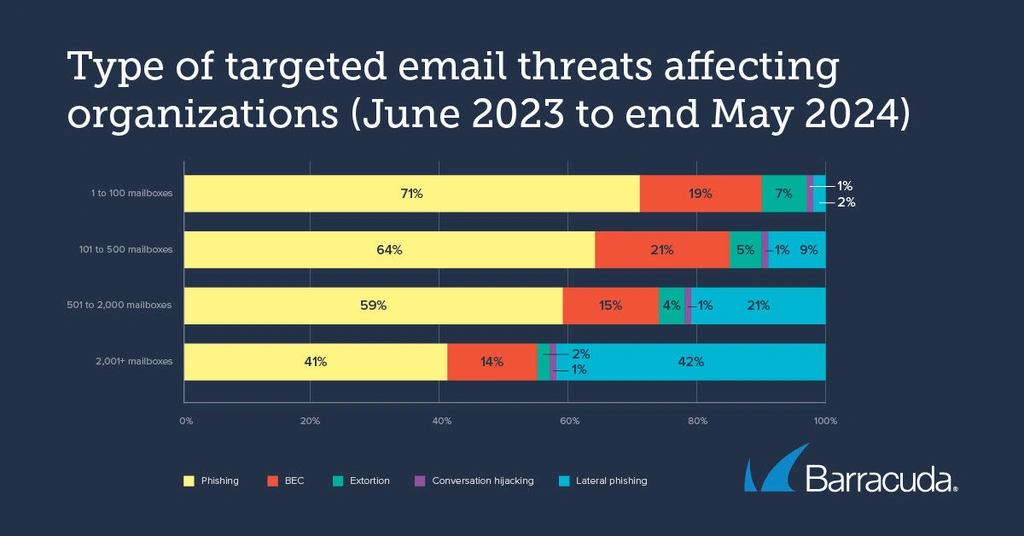
Targeted email attack profiles by company size
The data suggests that the prevalence of BEC and conversation hijacking stays relatively consistent regardless of company size.
However, the profile for other targeted email threats is more variable. For example, smaller companies are the most likely to be affected by phishing and extortion.
Phishing accounted for 71% of the targeted email attacks faced by companies with up to 100 mailboxes over 12 months, compared to 41% for larger organizations. Smaller companies also receive around three times as many extortion attacks as their larger counterparts. Extortion attacks comprised 7% of targeted incidents for the smallest businesses, compared to 2% for those with 2,000 mailboxes or more.
This may be in part because smaller organizations with fewer employees are less likely to have multiple layers of security in place to detect and block email threats such as phishing at the earliest possible stage. Their email filtering settings are often not configured to provide optimal security due to a lack of inhouse resources and expertise, which could allow more attacks to get through.
Lateral phishing targets larger firms
Lateral phishing, which may include spam or more sophisticated threats, are attacks that are sent to accounts across an organization from an already compromised internal account.
Just under half (42%) of the targeted email attack detections in the largest companies involved lateral phishing, compared to only 2% for the smallest organizations. This internal attack vector is a major risk for large businesses.
The prevalence of account compromises among larger businesses may reflect the fact that credentials for many companies are likely already available for purchase on the dark web, making lateral phishing a straightforward attack. Larger companies are attractive targets for cybercriminals because they potentially offer a greater return on investment. These organizations often hold vast amounts of valuable sensitive, confidential, and financial data.
Larger companies present numerous exploitation opportunities for cybercriminals. With more mailboxes and employees, there are significantly more potential points of entry for attackers. Additionally, these organizations often have multiple communication channels, including distribution lists, which can rapidly disseminate malicious messages across the business, effectively hiding within the high volume of internal traffic.
Employees regularly receive a high volume of email messages daily, making them more susceptible to cyber-attacks as they rush through their inboxes. They are more likely to trust email messages that appear to come from within the organization, even if the sender is unfamiliar to them. Cybercriminals can exploit these behavioral tendencies to spread lateral phishing messages more effectively.
Barracuda researchers have found that lateral phishing attacks are rarely targeted. Attackers are using the 'spray-and-pray' approach, and most messages resemble spam. Each lateral phishing attack 'campaign' can often involve thousands of messages. This means that it can take just a few incidents to really impact the results.
How to stay safe from email threats
Education is key to protecting your organization from email-based attacks — no matter if you're a small business with just a few employees or a large enterprise with hundreds of mailboxes. Use security awareness training to help keep everyone informed about the latest threats so they can easily spot suspicious emails. Employees should also keep an eye out for unusual activities in their accounts, which could be a sign of compromise, and report them right away.
It is also important to teach employees not to trust an email simply because it comes from a colleague. Include lateral phishing attacks as part of phishing simulation campaigns to help reinforce this message.
An AI-powered solution that helps detect and remediate account takeover attacks is another critical piece of protection you need to have in place to help effectively protect against today's sophisticated email threats. The tools help identify account takeover attacks, compromised accounts, and reconnaissance activities. Be sure to monitor for suspicious logins, rule changes, or unusual/malicious messages sent.
Internal email monitoring is also important. Most email gateways don't monitor internal mail. Make sure your email security solution is able to monitor internal mail for malicious intent.



Comments